If you’re a service provider streaming premium OTT video, chances are that as you read this blog, pirates are busy stealing — or at least trying to steal — content from your service to siphon your revenue. Even if you’ve managed to stay under the pirates’ radar till now, content owners are demanding that you comply with certain security requirements that require watermarking. Either way, piracy is impacting your industry… and watermarking (WM) is fast becoming an essential tool to securing your OTT business.
That’s why it’s not a question of if you need a WM solution, but rather which type of implementation makes the most sense for you. In this three-part blog series, we’ll help you navigate the watermarking world so that you can make a more informed decision.
In the second blog, we’ll use that know-how to compare the two main watermarking approaches – client and headend. You’ll learn which approach is more effective in combating leaks to piracy from OTT services, and no less important, the reasons why.
Once you are aware of the best WM approach, there still are a number of factors to consider in choosing the right solution. We’ll focus on a key consideration in blog #3, as we continue to accompany you along your watermarking journey. And we’ll follow that up with an in-depth watermarking guide that you won’t want to miss.
Forensic Watermarking: Tracking the Source of the Leak
Before diving in, let’s briefly remind ourselves how watermarking acts as a popular technology for tracking leaked video content through three basic steps.
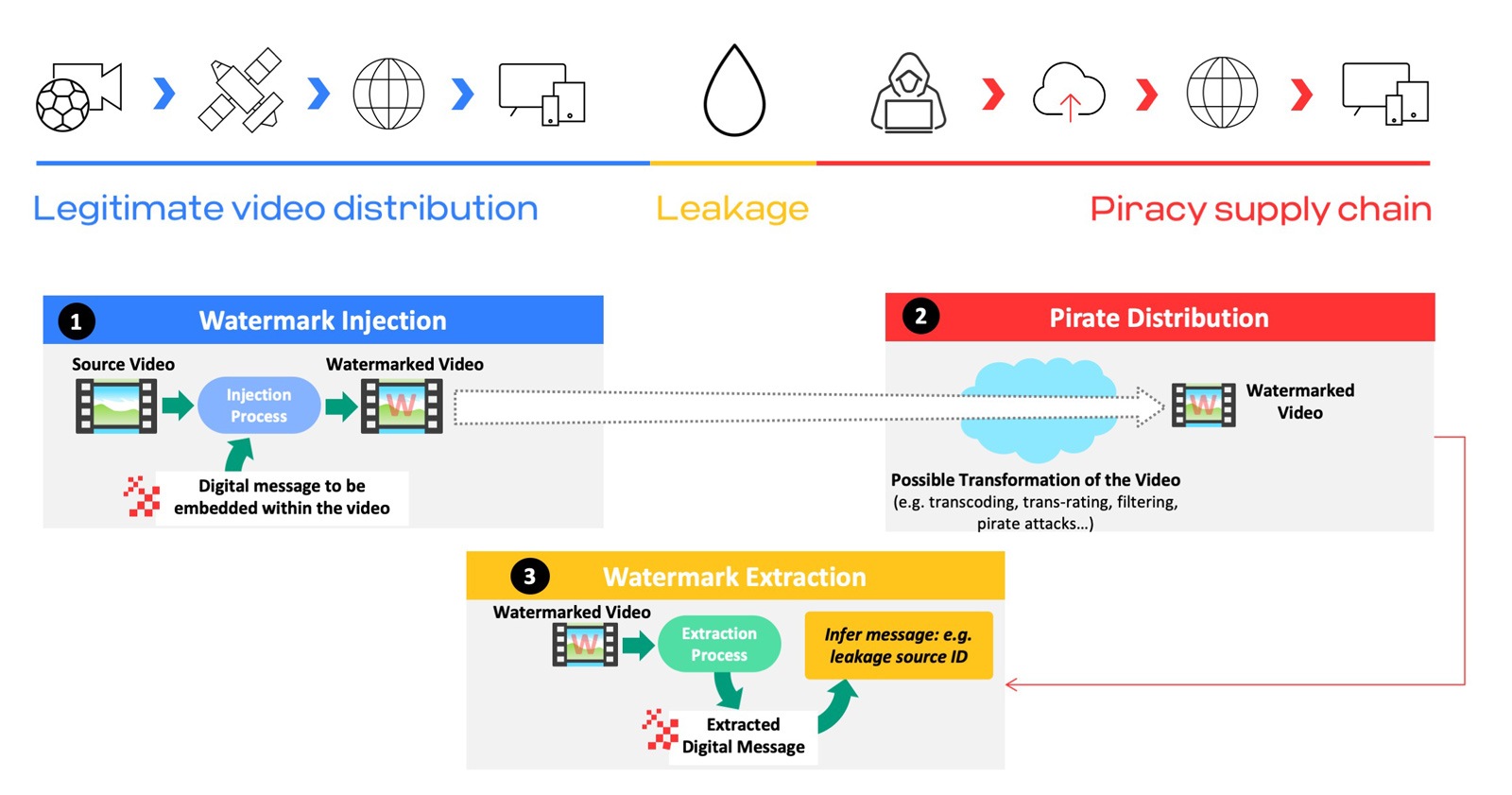
- Injection – You embed digital data (aka watermark), representing the subscriber or device’s ID, into the video stream.
- Pirate Distribution – After the video is leaked, pirates swoop in to manipulate and distribute it to viewers.
- Extraction – You locate the leaked video on the pirate’s service, and then extract the watermark to determine the source of the leak and (hopefully) take action.
Pirates’ Plan of Attack
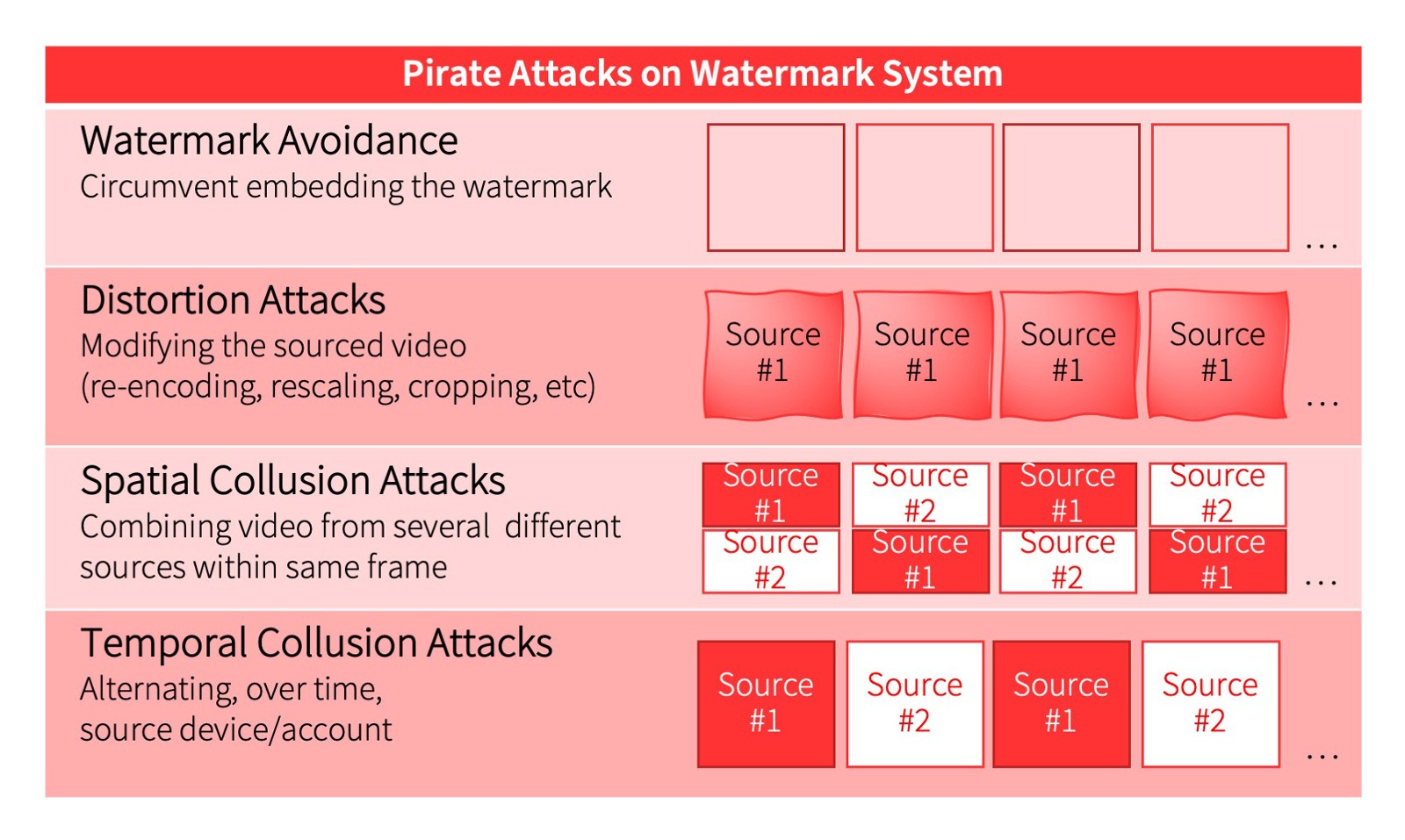
Piracy has been rampant in the broadcast domain for some time. But with OTT streaming on the rise, your business is also on the pirates’ map. So much so, that they have come up with several methods for attacking WM solutions that fall under four broad categories.
Avoidance: No WM, no problem
One of the easiest and most prevalent attack modes is when pirates disable the insertion of the watermark. This gives pirates a clean video version that is untraceable to the leakage source.
Pirates carry out avoidance attacks in one of three main ways.
- Device-side overlay tampering
Pirates can manipulate easily obtainable software on a client (consumer) device to:
- Prevent the WM image from being generated
- Create a modified or blank watermark image
- Circumvent the overlay process altogether
The bottom line. By bypassing WM insertion in the client, pirates ensure that the watermark will never appear on your leaked video.
- Signal blocking
Sometimes the headend automatically triggers a signal to embed the WM in the client. In that case, pirates can use common software to block the signal to the device and prevent the WM from appearing on your video.
- Content confiscation from the CDN
In this increasingly popular method, pirates buy scripts — programs that imitate client applications — to directly access content from your content delivery network (CDN). Easily obtainable on the dark web, these scripts often bypass DRM on the fly and so completely circumvent WM insertion in the client.
Distortion: If it’s messy, it’s hard to read
Another popular method is when pirates capture a perfect original video source and modify it, making the watermark unreadable upon extraction. All they need is common software that re-encodes, rescales, or crops the video. Even more rudimentary, pirates can place a camcorder in front of a screen, record the video, and distort the watermark by toying with the camera angle, room condition, or camera quality. Regardless of distortion method, the goal is the same – to make it tough for you to read the WM at extraction.
Spatial Collusion: The more sources the merrier
In this sophisticated, rarer attack, pirates feed multiple video sources into a single, off-the-shelf encoder, which then combines them on a frame-by-frame basis. The encoder combines the inputs via tiling, averaging, or blacking out methods. Similarly, pirates can deploy a majority attack or subtraction attack to interfere with your watermark. Helping you better understand these and other advanced methods is for another blog down the road.
Temporal Collusion: Combine and confuse
Pirates alternate, over time, the source device used to extract video streams to confuse your watermarking ID extraction system. For example, they may use device A for a few seconds, then switch to device B, followed by device C, and then back to B. This is also a complex and less prevalent method, since pirates need to synchronize input segments at the same bit rate and resolution to ensure that the transition is unnoticed by viewers.
A Moving Target
Once pirates realize you’ve tracked them down, they quickly counterattack, putting you back on the defensive in this never-ending cat and mouse game. Pirates, who are the source of the leakage, often sell the stolen content to many pirate services. Therefore, it’s in their business interest to constantly attack, in any possible way, the watermark and avoid detection. That’s why you need a solution that leverages intelligence, so that it can be enhanced to combat current and evolving attacks.
Narrowing Down your Weapon of Choice
Now that we’ve established the pirates’ rules of engagement in attacking WM, you’re ready to address the first big question: Which of the two predominant watermarking approaches – client- or headend-based – is most suitable to address the aforementioned pirate attacks on your OTT service?
In our next blog, we’ll discuss the factors you need to consider when evaluating a WM solution for your OTT service, and then compare the two approaches accordingly. Semi-spoiler alert: the decision is a no-brainer.
About the Author
Rinat Burdo, Principal Product Manager, is responsible for Synamedia’s Streaming Piracy Disruption solution. She has 14 years experience in product management and market intelligence, working for Fortune 500 companies and start-ups.